Ever wondered if you could bend the rules of a smart contract to your advantage? What if there was a way to leverage a contract's own logic against itself? Sounds like something out of a sci-fi movie, right? But it's a real, albeit dangerous, possibility in the world of blockchain: the reentrancy attack.
Let's be honest, navigating the world of smart contracts can feel like walking through a minefield. Understanding the intricacies of Solidity, gas optimization, and potential vulnerabilities is enough to make anyone's head spin. And even when you think you've got a handle on it all, lurking in the shadows are security risks that can wipe out your hard work in an instant.
This blog post aims to shine a light on the fascinating, and frankly, terrifying, world of reentrancy attacks. While we won't be advocating for malicious behavior, understanding how these attacks work is crucial for any developer or user interacting with decentralized applications. We'll explore the mechanics of reentrancy, discuss real-world examples, and, most importantly, outline strategies to prevent these vulnerabilities from creeping into your own smart contracts.
In essence, we'll cover what reentrancy attacks are, how they've been exploited in the past (like the infamous DAO hack), and the best practices to secure your smart contracts against them. We'll dive deep into preventative measures like checks-effects-interactions pattern, reentrancy guards, and gas limits, so you can confidently build robust and secure decentralized applications. Think of it as your ultimate guide to understanding and mitigating one of the most critical security risks in the blockchain space.
Understanding Reentrancy in Smart Contracts
The goal here is to break down the concept of reentrancy, explain how it works within the context of smart contracts, and why it's such a dangerous vulnerability. I remember the first time I encountered the term reentrancy.I was auditing a smart contract for a De Fi project, and I kept seeing recommendations to implement "reentrancy guards." At first, it just sounded like another buzzword. But the more I researched it, the more I realized how fundamental it was to smart contract security. Reentrancy is a type of vulnerability that occurs when a contract function calls another contract externally, and that external contract then calls back into the original functionbeforethe original function has completed its execution. Imagine a function designed to withdraw tokens. If a malicious contract can call this withdraw function recursivelyduringits execution, it can drain the contract's funds far beyond what it was initially authorized to withdraw.
Think of it like this: you're paying a bill, and as you're handing over the money, the person you're paying snatches some more while you're still counting out the original amount. The contract thinks it's still processing the initial withdrawal, but the attacker has already managed to initiate a second, and potentially many more, withdrawals. This is where the danger lies. The impact of a successful reentrancy attack can be devastating, ranging from significant financial losses to the complete compromise of a smart contract's functionality. Common mitigation strategies include implementing checks-effects-interactions pattern (where state changes are performedbeforeexternal calls), using reentrancy guards (modifiers that prevent recursive calls), and setting reasonable gas limits to prevent malicious actors from exploiting the vulnerability.
The Mechanics of a Reentrancy Attack
This section will dissect the technical details of how a reentrancy attack unfolds, explaining the steps involved from initiating the attack to draining the contract's funds. Reentrancy attacks exploit the way Ethereum smart contracts interact with each other. When a contract A calls a function in contract B, control is transferred to contract B. Contract B can then call back into contract A, provided it knows the address and function signature. The vulnerability arises when contract A doesn't properly update its statebeforemaking the external call to contract B. Let's illustrate with an example: imagine a contract with a `withdraw` function. This function first checks if the caller has enough balance, then transfers the funds to the caller, and finally updates the caller's balance to reflect the withdrawal. A malicious contract can exploit this process by calling the `withdraw` function, receiving the funds, and then,beforethe original function updates the user's balance, calling the `withdraw` function again. Because the balance hasn't been updated yet, the attacker can withdraw the funds multiple times.
This is possible due to the fact that the attacker's contract gains control during the external call and can re-enter the original contract. The key here is the order of operations. The vulnerable contract performs the transferbeforeupdating its state. This creates a window of opportunity for the attacker to re-enter the function and withdraw more funds than they are entitled to. Gas limits can sometimes mitigate this risk by limiting the number of operations that can be performed within a single transaction. However, sophisticated attackers can carefully craft their contracts to stay within the gas limit while still achieving their malicious goals. To prevent these attacks, it's critical to adhere to secure coding practices like the checks-effects-interactions pattern, and to employ reentrancy guards. By doing so, you can significantly reduce the risk of a reentrancy attack and protect your smart contract from exploitation.
The History and Myth of Reentrancy Attacks
This segment will explore the historical context of reentrancy attacks, focusing on the most famous example: The DAO hack. It will also debunk some common misconceptions surrounding these attacks. The DAO (Decentralized Autonomous Organization) was a pioneering attempt to create a venture capital fund that operated on the Ethereum blockchain. It was launched in 2016 and quickly attracted a significant amount of Ether (ETH). However, shortly after its launch, The DAO was subjected to a reentrancy attack that resulted in the theft of approximately $60 million worth of ETH. This attack was a major setback for the Ethereum community and highlighted the importance of smart contract security. The attacker exploited a flaw in The DAO's `split DAO` function, which allowed them to recursively call the function multiple times before the contract could update its internal state.
This allowed the attacker to drain a significant portion of The DAO's funds. The attack led to a hard fork of the Ethereum blockchain, which created Ethereum Classic (ETC) and Ethereum (ETH). The hard fork effectively reversed the attack and returned the stolen funds to their rightful owners. However, it also sparked a heated debate within the Ethereum community about the ethics of hard forks and the immutability of the blockchain. A common myth surrounding reentrancy attacks is that they are only a problem for complex De Fi protocols. In reality, any smart contract that makes external calls to other contracts is potentially vulnerable to reentrancy attacks, regardless of its complexity. Another myth is that gas limits can completely prevent reentrancy attacks. While gas limits can help to mitigate the risk, they are not a foolproof solution. Sophisticated attackers can still craft their contracts to stay within the gas limit while still achieving their malicious goals. Understanding the history and myths surrounding reentrancy attacks is crucial for developing secure smart contracts.
Hidden Secrets of Reentrancy Attacks
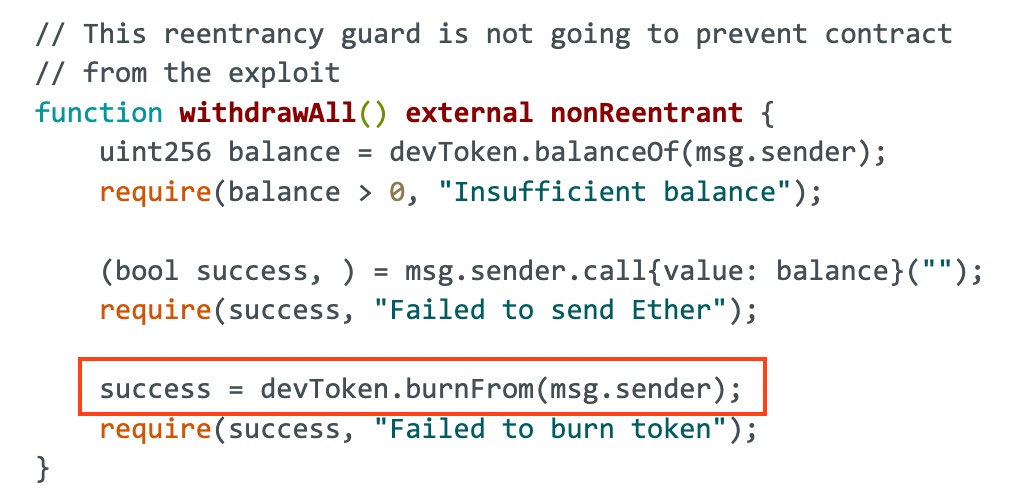
Let's dig deeper into some of the less obvious aspects of reentrancy, including the different types of reentrancy and potential attack vectors. While the classic example of reentrancy involves direct recursive calls within the same function, there are more subtle variations. One such variation iscross-function reentrancy. This occurs when one function in a contract calls an external contract, and that external contract then callsanotherfunction in the original contract. Even if the first function is protected by a reentrancy guard, the second function might still be vulnerable if it doesn't have its own guard. Another potential attack vector is through fallback functions. If a contract receives Ether without any associated data, its fallback function is executed. A malicious contract can exploit this by sending Ether to a vulnerable contract, triggering the fallback function, and then using the fallback function to re-enter the original contract.
This can bypass reentrancy guards that are only implemented on specific functions. Another hidden secret is that reentrancy attacks can be combined with other vulnerabilities to create more complex exploits. For example, an attacker might combine a reentrancy attack with an integer overflow or underflow to manipulate the contract's state in unexpected ways. It's also important to note that reentrancy attacks are not limited to Ethereum. They can occur on any blockchain platform that supports smart contracts with external calls. To protect against these hidden threats, it's essential to adopt a defense-in-depth approach. This means implementing multiple layers of security, including reentrancy guards, checks-effects-interactions pattern, and thorough code audits. You should also carefully consider the potential interactions between different functions in your contract and be aware of the risks associated with fallback functions. By understanding these hidden secrets, you can significantly improve the security of your smart contracts.
Recommendation of Reentrancy Attacks
Here's a practical recommendation on how to approach identifying and mitigating reentrancy vulnerabilities in your own code. Prevention is always better than cure, so let's focus on proactive measures. First and foremost, always follow the checks-effects-interactions pattern. This means that you should perform all necessary checksbeforemaking any state changes, and you should perform state changesbeforemaking any external calls. By doing so, you can minimize the window of opportunity for an attacker to exploit a reentrancy vulnerability. Second, use reentrancy guards. These are modifiers that prevent recursive calls to a function. There are several ways to implement reentrancy guards, but one common approach is to use a state variable that is set to `true` when the function is entered and set back to `false` when the function is exited. If the function is called recursively, the state variable will already be `true`, preventing the function from executing again.
Third, be cautious when making external calls to untrusted contracts. Always assume that the external contract is malicious and can attempt to re-enter your contract. Fourth, use gas limits to limit the amount of gas that can be consumed by a transaction. This can help to prevent attackers from exploiting reentrancy vulnerabilities by making excessively long recursive calls. Finally, conduct thorough code audits. Have your code reviewed by experienced security auditors who can identify potential vulnerabilities that you may have missed. Code audits are an essential part of the development process and can help to ensure that your smart contracts are secure. By following these recommendations, you can significantly reduce the risk of reentrancy attacks and protect your smart contracts from exploitation. Remember, security is an ongoing process, not a one-time event. Stay vigilant and continuously monitor your contracts for potential vulnerabilities.
Checks-Effects-Interactions Pattern
Let's break down the checks-effects-interactions pattern and see how it directly relates to preventing reentrancy attacks. This pattern, often referred to as CEI, is a fundamental principle in smart contract development for writing secure code. The core idea is to structure your functions in a specific order to minimize the risk of vulnerabilities like reentrancy. Let's dissect each part: Checks: This involves validating all inputs and preconditions before proceeding. For example, checking if the caller has sufficient balance, if the contract is in the correct state, or if any other necessary conditions are met. The key here is to ensure that all potential issues are identifiedbeforemaking any changes to the contract's state. Effects: This is where you update the contract's internal state. This includes modifying balances, updating data structures, and setting flags. The critical point here is to make these state changesbeforemaking any external calls. This way, even if an external contract attempts to re-enter your contract, the state will already be updated, preventing the attacker from exploiting a reentrancy vulnerability.
Interactions: This is where you interact with external contracts or send Ether to other addresses. This should always be thelaststep in your function. By making external calls only after the state has been updated, you can significantly reduce the risk of reentrancy attacks. Let's consider an example: a vulnerable `withdraw` function might look like this: 1. Send Ether to the caller.
2. Update the caller's balance. A secure `withdraw` function using the checks-effects-interactions pattern would look like this:
1. Check if the caller has sufficient balance.
2. Update the caller's balance.
3. Send Ether to the caller. By following this pattern, you can ensure that your smart contracts are more resistant to reentrancy attacks. The checks-effects-interactions pattern is not a silver bullet, but it is a crucial step in writing secure smart contracts. Always strive to adhere to this pattern and combine it with other security best practices to maximize the protection of your contracts.
Tips for Reentrancy Attacks
This section will provide practical tips and tricks for preventing reentrancy attacks, including code examples and best practices. One of the most effective techniques is to use a reentrancy guard. A reentrancy guard is a modifier that prevents a function from being called recursively. This can be implemented by using a state variable that is set to `true` when the function is entered and set back to `false` when the function is exited. If the function is called recursively, the state variable will already be `true`, preventing the function from executing again. Here's an example of how to implement a reentrancy guard using the `non Reentrant` modifier from Open Zeppelin: ```solidity import "@openzeppelin/contracts/security/Reentrancy Guard.sol"; contract My Contract is Reentrancy Guard { function withdraw() public non Reentrant { // Your code here } } ``` Another important tip is to avoid making external calls in the middle of critical operations. If you need to make an external call, do itafteryou have updated the state of your contract.
This will prevent an attacker from exploiting a reentrancy vulnerability by calling back into your contract before the state has been updated. It's also crucial to be aware of the potential risks associated with fallback functions. If your contract has a fallback function, it can be triggered when your contract receives Ether without any associated data. A malicious contract can exploit this by sending Ether to your contract, triggering the fallback function, and then using the fallback function to re-enter your contract. To prevent this, you should carefully consider the logic of your fallback function and ensure that it does not contain any vulnerabilities. Finally, always conduct thorough code audits. Have your code reviewed by experienced security auditors who can identify potential vulnerabilities that you may have missed. Code audits are an essential part of the development process and can help to ensure that your smart contracts are secure. By following these tips, you can significantly reduce the risk of reentrancy attacks and protect your smart contracts from exploitation.
Gas Limits and Reentrancy Attacks
Let's investigate the role of gas limits in preventing or mitigating reentrancy attacks. While gas limits aren't a foolproof solution, they can play a significant role in limiting the impact of certain attacks. Each transaction on the Ethereum network requires a certain amount of gas to execute. Gas limits are a way to limit the amount of gas that a transaction can consume. If a transaction exceeds the gas limit, it will be reverted, and any state changes will be undone. This can be used to prevent attackers from exploiting reentrancy vulnerabilities by making excessively long recursive calls. Imagine a reentrancy attack that attempts to drain all the funds from a vulnerable contract. If the attacker sets a low gas limit, the transaction might be reverted before they can drain all the funds. However, it's important to note that gas limits are not a silver bullet. Sophisticated attackers can carefully craft their contracts to stay within the gas limit while still achieving their malicious goals.
For example, they might optimize their code to reduce the amount of gas it consumes, or they might break the attack into multiple smaller transactions, each with its own gas limit. Another limitation of gas limits is that they can also affect legitimate users. If a user sets a gas limit that is too low, their transaction might be reverted even if it is not malicious. This can be frustrating for users and can make it difficult to use your smart contracts. To effectively use gas limits to mitigate reentrancy attacks, it's essential to carefully consider the potential gas consumption of your functions and set reasonable gas limits that will allow legitimate users to use your contracts while still preventing attackers from exploiting vulnerabilities. It's also important to remember that gas limits should be used in conjunction with other security measures, such as reentrancy guards and the checks-effects-interactions pattern. By combining these different approaches, you can significantly improve the security of your smart contracts.
Fun Facts of Reentrancy Attacks
Here's some interesting and perhaps surprising facts about reentrancy attacks to add some flavor to our discussion. Did you know that the term "reentrancy" actually comes from the world of operating systems? In operating systems, reentrancy refers to a function that can be safely called by multiple threads or processes simultaneously. However, in the context of smart contracts, reentrancy is a vulnerability, not a feature. Another fun fact is that the DAO hack was not the first reentrancy attack on Ethereum. There were several smaller attacks that occurred before the DAO hack, but they didn't receive as much attention. The DAO hack was a watershed moment because it resulted in the theft of a significant amount of Ether and highlighted the importance of smart contract security. It also sparked a heated debate within the Ethereum community about the ethics of hard forks and the immutability of the blockchain.
Another interesting fact is that reentrancy attacks are not limited to Ethereum. They can occur on any blockchain platform that supports smart contracts with external calls. However, Ethereum is the most popular platform for smart contracts, so it has been the target of the most reentrancy attacks. It's also worth noting that reentrancy attacks are not always intentional. Sometimes, developers can accidentally introduce reentrancy vulnerabilities into their code without realizing it. This is why it's so important to conduct thorough code audits and to follow secure coding practices. Finally, it's interesting to note that the research and development of reentrancy guards and other security measures have significantly improved the security of smart contracts over the years. While reentrancy attacks are still a threat, they are much more difficult to execute today than they were in the early days of Ethereum. By understanding these fun facts, you can gain a deeper appreciation for the history and evolution of smart contract security.
How to Defend Against Reentrancy Attacks
This section will focus on the practical steps developers can take to defend their smart contracts against reentrancy attacks. As we've discussed, the checks-effects-interactions pattern is a cornerstone of secure smart contract development. Make absolutely sure that your state updates occurbeforeany external calls. But let's go beyond that and look at specific techniques and code examples. 1.Use Reentrancy Guards: This is your primary line of defense. Utilize the `@openzeppelin/contracts/security/Reentrancy Guard.sol` library. It provides a simple and effective way to prevent reentrancy. Here's a reminder on how to use it: ```solidity import "@openzeppelin/contracts/security/Reentrancy Guard.sol"; contract My Contract is Reentrancy Guard { function withdraw() public non Reentrant { // Your secure withdraw logic here } } ```
2.Pull over Push: Instead of pushing Ether to a user's address using `transfer` or `send`, have the userpullthe Ether from your contract. This eliminates the external call from your contract, reducing the risk of reentrancy.
3.Consider using the `transfer()` function with caution: The `transfer()` function has a fixed gas limit of 2300 gas. While this might seem like a safety mechanism against reentrancy, it's not reliable. A malicious contract can still execute a fallback function within that gas limit. It's generally recommended to use `call()` with a specified gas amount, but be aware of the potential risks and ensure you handle the return value.
4.Implement Gas Limits (But Don't Rely Solely on Them): As mentioned before, gas limits can help, but they are not a foolproof solution. Set reasonable gas limits to prevent excessively long recursive calls.
5.Code Audits and Formal Verification: Invest in professional code audits. Experienced security auditors can identify vulnerabilities that you might have missed. Formal verification is another powerful technique that uses mathematical methods to prove the correctness of your code. By implementing these defensive measures, you can significantly reduce the risk of reentrancy attacks and protect your smart contracts from exploitation. Remember, security is an ongoing process, so stay vigilant and continuously monitor your contracts for potential vulnerabilities.
What If Reentrancy Attacks Occur?
Let's explore what actions you should take if you suspect or confirm that your smart contract is under a reentrancy attack. The first and most crucial step is topause the contract immediately. Most well-designed contracts have a "pause" functionality that allows the owner or a designated administrator to temporarily halt all activity. This prevents further exploitation of the vulnerability. If your contract doesn't have a pause function, consider implementing one as soon as possible. It's a vital safety net. Next, analyze the attack to understand the extent of the damage. Identify which functions were exploited, how much Ether or tokens were stolen, and the potential impact on your users. Examine the transaction history and logs to gather as much information as possible. Then,*contact the relevant authorities and security experts. Report the attack to the blockchain security community and consider reaching out to law enforcement agencies if the attack involves significant financial losses. Seek expert advice from security auditors and incident response teams. They can help you understand the vulnerability, contain the damage, and develop a remediation plan.
After that,develop and deploy a fix. Once you have identified the root cause of the reentrancy vulnerability, develop a fix and thoroughly test it in a secure environment. Consider deploying a new version of the contract with the fix and migrating the remaining funds to the new contract. Finally, communicate transparently with your users. Inform them about the attack, the steps you are taking to resolve the issue, and the potential impact on their funds. Transparency is crucial for maintaining trust and confidence in your project. While dealing with a reentrancy attack can be a stressful and challenging experience, it's important to remain calm, take decisive action, and learn from the experience. Implement robust security measures in your future contracts to prevent similar attacks from occurring again. Reentrancy attacks are a serious threat, but with the right preparation and response plan, you can mitigate the damage and protect your project and users.
Listicle of Reentrancy Attacks
Here’s a listicle summarizing key aspects of reentrancy attacks to help you remember the crucial points:
1.Definition: A reentrancy attack is a vulnerability that occurs when a contract function calls another contract externally, and that external contract then calls back into the original functionbeforethe original function has completed its execution.
2.The DAO Hack: The most famous example of a reentrancy attack, resulting in the theft of approximately $60 million worth of ETH.
3.Checks-Effects-Interactions Pattern: The fundamental principle of secure smart contract development, ensuring that state updates occurbeforeany external calls.
4.Reentrancy Guards: Modifiers that prevent recursive calls to a function, providing a primary line of defense against reentrancy attacks.
5.Pull over Push: A technique that reduces the risk of reentrancy by having userspull Ether from your contract instead of pushing it to them.
6.Gas Limits: Can help mitigate the impact of reentrancy attacks by limiting the amount of gas that a transaction can consume, but are not a foolproof solution.
7.Code Audits: Essential for identifying potential vulnerabilities that you may have missed.
8.Defense-in-Depth: Implement multiple layers of security, including reentrancy guards, checks-effects-interactions pattern, and thorough code audits.
9.Pause Function: A vital safety net that allows the owner or a designated administrator to temporarily halt all activity in the contract.
10.Transparency: Communicate openly and honestly with your users about any security incidents and the steps you are taking to resolve them.
Question and Answer
Here are some common questions and answers related to reentrancy attacks: *Q: What is the main cause of reentrancy vulnerabilities?
A: The main cause is making external callsbeforeupdating the contract's internal state. This creates a window of opportunity for an attacker to re-enter the function and manipulate the contract's state.*Q: How does the checks-effects-interactions pattern prevent reentrancy attacks?
A: By performing checks and updating the contract's statebeforemaking any external calls, the checks-effects-interactions pattern ensures that the contract's state is consistent even if an external contract attempts to re-enter it.*Q: Can gas limits completely prevent reentrancy attacks?
A: No, gas limits can help mitigate the impact of reentrancy attacks, but they are not a foolproof solution. Sophisticated attackers can craft their contracts to stay within the gas limit while still achieving their malicious goals.*Q: What is a reentrancy guard and how does it work?
A: A reentrancy guard is a modifier that prevents a function from being called recursively. It typically uses a state variable that is set to `true` when the function is entered and set back to `false` when the function is exited. If the function is called recursively, the state variable will already be `true`, preventing the function from executing again.
Conclusion of How to Use Reentrancy Attacks for Maximum Benefits
Reentrancy attacks are a serious threat to smart contract security, but with a thorough understanding of the vulnerability and the implementation of robust security measures, you can significantly reduce the risk of exploitation. By adhering to the checks-effects-interactions pattern, using reentrancy guards, and conducting thorough code audits, you can build more secure and resilient decentralized applications. Remember that security is an ongoing process, so stay vigilant and continuously monitor your contracts for potential vulnerabilities. The knowledge gained here will serve as a valuable foundation for navigating the complex landscape of blockchain security and protecting your projects from reentrancy attacks and other potential threats.