Imagine your digital piggy bank suddenly emptying itself, not because you withdrew the money, but because someone cleverly tricked the system. That's the essence of a reentrancy attack – a sneaky exploit that has plagued the world of smart contracts, leading to significant losses and a lot of headaches.
The potential for financial damage and loss of trust in blockchain technology due to these attacks is a real concern. Developers pour their hearts into creating innovative decentralized applications, but a single vulnerability can be exploited to drain funds, jeopardizing the entire project and the users who rely on it.
This post will delve into the mechanics of reentrancy attacks, explaining how they work, why they're so dangerous, and what measures can be taken to prevent them. Understanding these attacks is crucial for anyone involved in developing or interacting with smart contracts, ensuring a safer and more secure blockchain ecosystem.
In essence, reentrancy attacks exploit vulnerabilities in smart contracts, allowing malicious actors to repeatedly withdraw funds before the contract can update its balance. We'll explore the technical details, real-world examples, preventative measures like checks-effects-interactions pattern, and the ongoing evolution of security practices in the blockchain space. Keywords: reentrancy attack, smart contract, vulnerability, security, blockchain, Ethereum, Solidity, checks-effects-interactions, security audits.
Understanding the Reentrancy Vulnerability: A Personal Encounter
My first encounter with the concept of reentrancy attacks was during a security audit of a decentralized exchange (DEX) project. I was fairly new to smart contract security, and I remember feeling a bit overwhelmed by the complexity of the code. We were using Solidity, and the DEX allowed users to swap tokens. One of the functions involved transferring tokens between users and updating their balances. At first glance, everything seemed fine. But as I dug deeper, I realized there was a potential flaw in the logic.
The contract was vulnerable because it transferred fundsbeforeupdating the user's balance. Picture this: A malicious contract calls the vulnerable contract's withdraw function. Before the original withdrawal transaction can complete (updating the balance), the malicious contractre-entersthe vulnerable contract, calling the withdraw function again. Because the original balance hasn't been updated yet, the malicious contract can withdraw funds multiple times, essentially draining the contract's balance beyond what it's supposed to allow. This is called recursion.
Reentrancy attacks happen when a smart contract calls another contract, and the called contract (or a contract it subsequently calls) makes a call back to the original contractbeforethe original call has completed. This can lead to unexpected and undesirable behavior, particularly in contracts that manage funds. The key vulnerability lies in the order of operations: if a contract updates its state (like a user's balance)aftersending funds, it creates a window of opportunity for the recipient to call back and exploit the outdated state. This simple flaw, if not properly addressed, can have catastrophic consequences.
The Mechanics of a Reentrancy Attack: How It Unfolds
At its heart, a reentrancy attack hinges on the concept of a smart contract calling another contract. This is a common and essential feature of decentralized applications (d Apps), allowing for complex interactions between different components of the ecosystem. However, this interaction also creates a potential vulnerability. Imagine contract A, which manages user balances and allows them to withdraw funds. Now, imagine contract B, a malicious contract designed to exploit contract A.
The attack unfolds as follows:
Contract B calls contract A's `withdraw` function, requesting a specific amount of funds.
Contract A initiates the transfer of funds to contract B's address.
Crucially,beforecontract A updates the user's balance to reflect the withdrawal, contract B's fallback function is triggered (or another function in contract B is executed).
Inside this fallback function, contract Bre-enterscontract A, calling the `withdraw` functionagain.
Because contract A hasn't updated the user's balance yet, it still believes contract B has the original amount available for withdrawal.
Contract B withdraws funds again, essentially exploiting the outdated state of contract A.
This process can be repeated multiple times, allowing contract B to drain contract A's funds beyond what it's legitimately entitled to.
The DAO Hack: A Historic Lesson in Reentrancy
The most infamous example of a reentrancy attack is undoubtedly the DAO hack in 2016. The DAO (Decentralized Autonomous Organization) was a groundbreaking project designed to be a venture capital fund run entirely by code on the Ethereum blockchain. It held a significant amount of Ether, making it a prime target for attackers. The DAO used a "split" function to allow members to exit the DAO and withdraw their Ether. This function was vulnerable to a reentrancy attack.
An attacker exploited this vulnerability to repeatedly withdraw Ether from the DAO before the DAO's contract could update its balance. The attacker essentially called the `split` function multiple times within a single transaction, draining a significant portion of the DAO's funds. This event had a profound impact on the Ethereum community, leading to a hard fork of the Ethereum blockchain to recover the stolen funds. The DAO hack serves as a stark reminder of the devastating consequences of reentrancy vulnerabilities and the importance of rigorous security audits. The myth surrounding the DAO became a legend, and it shows everyone that it will be a problem that they will need to consider when developing smart contract, and that it will be something to remember for a long time.
Unveiling the Secret: The Importance of Order of Operations
The secret to understanding and preventing reentrancy attacks lies in understanding the critical importance of the order of operations within your smart contract functions. The key is to ensure that state variables are updatedbeforeany external calls are made. This is often referred to as the "Checks-Effects-Interactions" pattern. Let's break it down:
Checks: Perform all necessary checks to ensure the transaction is valid. This includes verifying user permissions, validating input parameters, and ensuring sufficient funds are available.
Effects: Update the state variables of the contract to reflect the changes resulting from the transaction. This includes updating user balances, modifying contract storage, and recording relevant events.
Interactions: Make any external calls to other contracts or send Ether to external accounts.
By following this pattern, you can significantly reduce the risk of reentrancy attacks. If you update the user's balancebeforesending them the funds, even if they re-enter the contract, they will only be able to withdraw the amount that is actually available to them. This simple change in the order of operations can make all the difference.
Recommendations for Preventing Reentrancy Attacks
Preventing reentrancy attacks requires a multi-faceted approach, combining secure coding practices, thorough testing, and comprehensive security audits. Here are some key recommendations:
Implement the Checks-Effects-Interactions pattern consistently throughout your smart contracts.
Use reentrancy guard modifiers, such as the `@reentrancy Guard` modifier in Open Zeppelin, to prevent re-entrant calls to vulnerable functions.
Consider using "pull-over-push" payment mechanisms, where users are responsible for withdrawing their funds rather than the contract pushing funds to them.
Perform thorough unit and integration tests to identify potential reentrancy vulnerabilities.
Engage reputable security auditors to review your code and identify any hidden flaws.
Stay up-to-date with the latest security best practices and vulnerabilities in the smart contract ecosystem.
Remember, security is an ongoing process, not a one-time fix. Continuously monitor your contracts for suspicious activity and be prepared to respond quickly to any potential threats. By taking a proactive and vigilant approach to security, you can help protect your smart contracts and your users from the devastating consequences of reentrancy attacks.
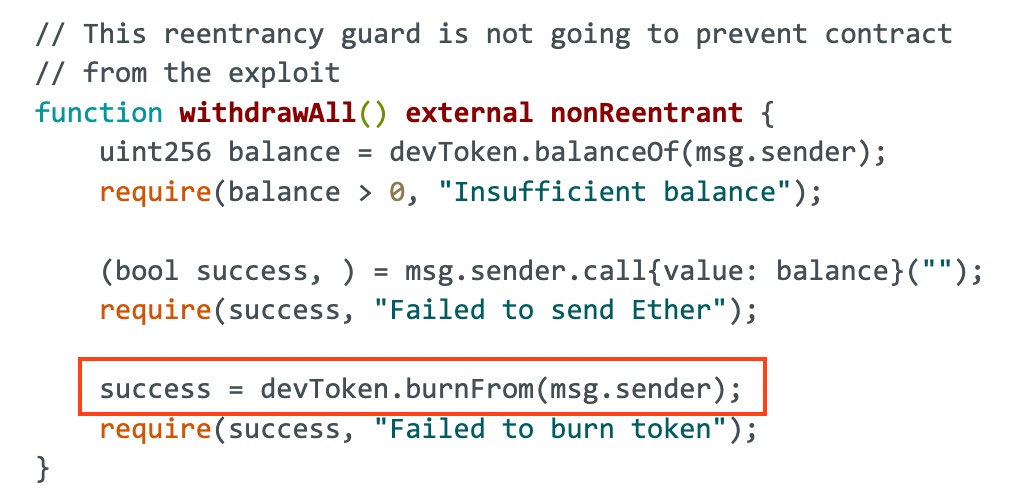
Understanding Reentrancy Guard Modifiers: Your First Line of Defense
Reentrancy guard modifiers are a powerful tool for preventing reentrancy attacks. These modifiers act as a gatekeeper, preventing a function from being called again before the first invocation has completed. They typically work by using a state variable to track whether a function is currently executing. If the function is called again while the state variable indicates that it's already running, the second call will be blocked.
Open Zeppelin provides a widely used `@reentrancy Guard` modifier that can be easily integrated into your Solidity contracts. To use it, you simply import the `Reentrancy Guard` contract and add the modifier to any functions that are susceptible to reentrancy attacks. For example:
```solidity
import "@openzeppelin/contracts/security/Reentrancy Guard.sol";
contract My Contract is Reentrancy Guard {
// ...
function withdraw(uint amount) public payable non Reentrant {
// ...
// Transfer funds and update balance
// ...
}
}
```
The `non Reentrant` modifier ensures that the `withdraw` function can only be called once at a time, preventing re-entrant calls from exploiting the contract.
Advanced Mitigation Techniques: Beyond the Basics
While the Checks-Effects-Interactions pattern and reentrancy guard modifiers are essential, there are also more advanced techniques that can be used to mitigate reentrancy attacks. One such technique is to use stateless contracts. Stateless contracts do not store any data on the blockchain. Instead, they rely on input parameters and external data sources to perform their functions. Because they do not maintain any internal state, they are inherently immune to reentrancy attacks.
Another approach is to use "gas limits" to restrict the amount of gas that can be consumed by external calls. By setting a gas limit that is lower than the amount required to execute a re-entrant call, you can prevent the attacker from exploiting the vulnerability. However, this approach can be difficult to implement correctly, as it requires careful estimation of gas costs and can potentially break legitimate functionality. It's also important to note that gas limits can change over time, so it's crucial to monitor and adjust them as needed. Therefore, using gas limits requires careful analysis to ensure that the gas limit is enough for normal operation, while still guarding from attacks.
The Role of Formal Verification: Proving Your Contract's Security
Formal verification is a rigorous technique that uses mathematical methods to prove the correctness of a smart contract's code. It involves creating a formal specification of the contract's intended behavior and then using automated tools to verify that the code meets that specification. Formal verification can be used to identify a wide range of vulnerabilities, including reentrancy attacks, overflow errors, and logic flaws. While formal verification can be time-consuming and expensive, it provides a high degree of assurance that your smart contract is secure.
There are several formal verification tools available for Solidity contracts, including Certora, Mythril, and Securify. These tools use different techniques, such as symbolic execution and model checking, to analyze the code and identify potential vulnerabilities. The process typically involves annotating the code with formal specifications and then running the verification tool to check that the code satisfies those specifications. If the tool finds any violations, it will provide a detailed report that can be used to fix the vulnerabilities.
Fun Facts About Reentrancy Attacks
Did you know that the term "reentrancy" comes from the world of operating systems? In operating systems, reentrancy refers to a program or subroutine that can be safely called again while it is already running. However, in the context of smart contracts, reentrancy has a much more negative connotation. Another fun fact is that reentrancy attacks are not unique to Ethereum. They can occur on any blockchain platform that supports smart contracts and allows for external calls between contracts.
Furthermore, many developers believe that reentrancy is a "solved problem" due to the widespread adoption of the Checks-Effects-Interactions pattern and reentrancy guard modifiers. However, new and creative reentrancy attack vectors continue to emerge, highlighting the importance of staying vigilant and continuously improving security practices. The rise of new programming paradigms and domain also introduces some level of uncertainty, and developers and security auditors need to stay vigilant to ensure that reentrancy attacks are mitigated.
How to Audit for Reentrancy Vulnerabilities: A Step-by-Step Guide
Auditing for reentrancy vulnerabilities requires a systematic approach and a deep understanding of smart contract security. Here's a step-by-step guide:
1.Code Review: Start by carefully reviewing the code, paying close attention to any functions that make external calls. Look for instances where state variables are updated after the external call.
2.Identify Potential Attack Vectors: Consider how an attacker could potentially re-enter the contract during the execution of a vulnerable function. Think about the different ways an attacker could trigger the external call and exploit the outdated state.
3.Manual Testing: Write unit and integration tests to simulate reentrancy attacks. Use tools like Remix or Hardhat to deploy and interact with your contracts.
4.Automated Analysis: Use automated security analysis tools like Slither, Mythril, and Securify to identify potential reentrancy vulnerabilities. These tools can help you find flaws that might be missed during manual code review and testing.
5.Formal Verification: If you require a high degree of assurance, consider using formal verification tools to prove the correctness of your contract's code.
6.Document Your Findings: Keep detailed records of your audit process, including any vulnerabilities you identified and the steps you took to mitigate them. This documentation will be valuable for future audits and for demonstrating the security of your contracts to potential users and investors.
What If Reentrancy Attacks Were Never Discovered?
Imagine a world where reentrancy attacks were never discovered. The landscape of blockchain and smart contracts would look drastically different, and likely much more unstable. Here's a glimpse into that alternative reality:
Decentralized Finance (De Fi) would be far less trustworthy. De Fi protocols rely heavily on the secure execution of smart contracts. Without awareness of reentrancy vulnerabilities, many De Fi platforms would be vulnerable to exploits, leading to massive losses and a loss of confidence in the entire ecosystem.
Adoption of blockchain technology would be significantly slower. The constant threat of reentrancy attacks would deter many individuals and institutions from adopting blockchain technology.
Security audits would be less effective. Without a focus on reentrancy vulnerabilities, security audits would miss a critical class of exploits, leaving smart contracts exposed to significant risks.
Innovation in smart contract development would be stifled. Developers would be hesitant to explore new and innovative smart contract designs, fearing the potential for reentrancy vulnerabilities.
The Ethereum ecosystem might have fractured beyond repair. The DAO hack, caused by a reentrancy vulnerability, already had a profound impact on the Ethereum community. Without a broader understanding of these attacks, similar incidents could have led to further fragmentation and a loss of confidence in Ethereum.
Listicle: Top 5 Ways to Prevent Reentrancy Attacks
Here are the top 5 ways to prevent reentrancy attacks:
1.Implement the Checks-Effects-Interactions Pattern: Always update state variablesbeforemaking external calls.
2.Use Reentrancy Guard Modifiers: Utilize modifiers like `@reentrancy Guard` from Open Zeppelin to prevent re-entrant calls.
3.Favor Pull-Over-Push Payment Mechanisms: Allow users to withdraw their funds instead of pushing funds to them.
4.Conduct Thorough Security Audits: Engage reputable security auditors to review your code for potential vulnerabilities.
5.Stay Updated on Security Best Practices: Continuously learn about the latest security threats and best practices in the smart contract ecosystem.
By following these five steps, you can significantly reduce the risk of reentrancy attacks and protect your smart contracts from exploitation.
Question and Answer about Reentrancy Attacks
Here are some frequently asked questions about reentrancy attacks:Q: What is a reentrancy attack?
A: A reentrancy attack is a type of smart contract vulnerability that allows an attacker to repeatedly call a function before the initial call has completed, potentially leading to unexpected and undesirable behavior, such as draining funds from the contract.
Q: Why are reentrancy attacks so dangerous?
A: Reentrancy attacks can lead to significant financial losses, damage to the reputation of the project, and a loss of trust in the blockchain ecosystem.
Q: How can I prevent reentrancy attacks in my smart contracts?
A: You can prevent reentrancy attacks by implementing the Checks-Effects-Interactions pattern, using reentrancy guard modifiers, favoring pull-over-push payment mechanisms, and conducting thorough security audits.
Q: Are reentrancy attacks only a problem on Ethereum?
A: No, reentrancy attacks can occur on any blockchain platform that supports smart contracts and allows for external calls between contracts.
Conclusion of How Reentrancy Attacks Works and Why It’s Important
Reentrancy attacks are a serious threat to the security of smart contracts and the overall integrity of the blockchain ecosystem. Understanding how these attacks work, and implementing appropriate preventative measures, is crucial for anyone involved in developing or interacting with smart contracts. By following best practices like the Checks-Effects-Interactions pattern, using reentrancy guard modifiers, and conducting thorough security audits, we can create a safer and more secure blockchain world. The future of decentralized applications depends on our collective commitment to security.