Imagine your digital vault being emptied not by a clever thief breaking in, but by a mischievous loophole that keeps handing them more money before they've even left the building. Sounds wild, right? This is essentially what a reentrancy attack does in the world of smart contracts, and it's a threat every developer (and user) should understand.
The prospect of writing secure smart contracts can feel overwhelming. The complexity of decentralized applications, combined with the high stakes of dealing with real-world value, can create a sense of anxiety. Knowing where to start, what to prioritize, and how to effectively protect your code from malicious actors can be a real challenge.
This guide is for anyone new to smart contract security, specifically focusing on reentrancy attacks. Whether you're a budding blockchain developer, a curious investor, or simply someone interested in the security of decentralized applications, this post will break down the basics of reentrancy attacks in an easy-to-understand way.
We'll start with the fundamental concepts of reentrancy, then explore how these attacks are executed, and finally, discuss common defense mechanisms. You'll gain a solid understanding of this critical vulnerability and learn how to prevent it from wreaking havoc on your smart contracts. Key terms we'll cover include: smart contracts, Solidity, Ethereum, vulnerability, security, attack vectors, and best practices.
What is a Reentrancy Attack?
This section will explain the core concept of a reentrancy attack. Think of it like this: a function in a smart contract calls an external contract (or address). This external contract then turns around and calls back the original functionbeforethe original function has finished executing. The target audience here is anyone who needs a simple, digestible explanation. I remember the first time I heard about reentrancy attacks. I was working on a simple De Fi project, a basic lending protocol. We had a function that allowed users to withdraw their collateral. We thought we had everything covered – checks to ensure sufficient balance, proper accounting of the withdrawn amount. But then, during a security audit, we were hit with the reality of reentrancy. The auditor explained how a malicious contract could repeatedly call our withdrawal function before we could update the user's balance, essentially draining the contract dry. It was a wake-up call. We realized that the seemingly simple act of calling an external contract opened up a whole new world of potential vulnerabilities. This experience hammered home the importance of understanding reentrancy attacks and the common patterns that make smart contracts susceptible. It's not just about writing code that works; it's about writing code that is resilient to malicious exploitation. A reentrancy attack exploits this callback mechanism to repeatedly execute parts of the original function, often leading to unintended consequences like draining funds or manipulating data. It's like a loophole in the system that allows a malicious actor to take advantage of a delayed update. Understanding this fundamental concept is the first step to writing secure smart contracts.
How Reentrancy Attacks Work: A Step-by-Step Example
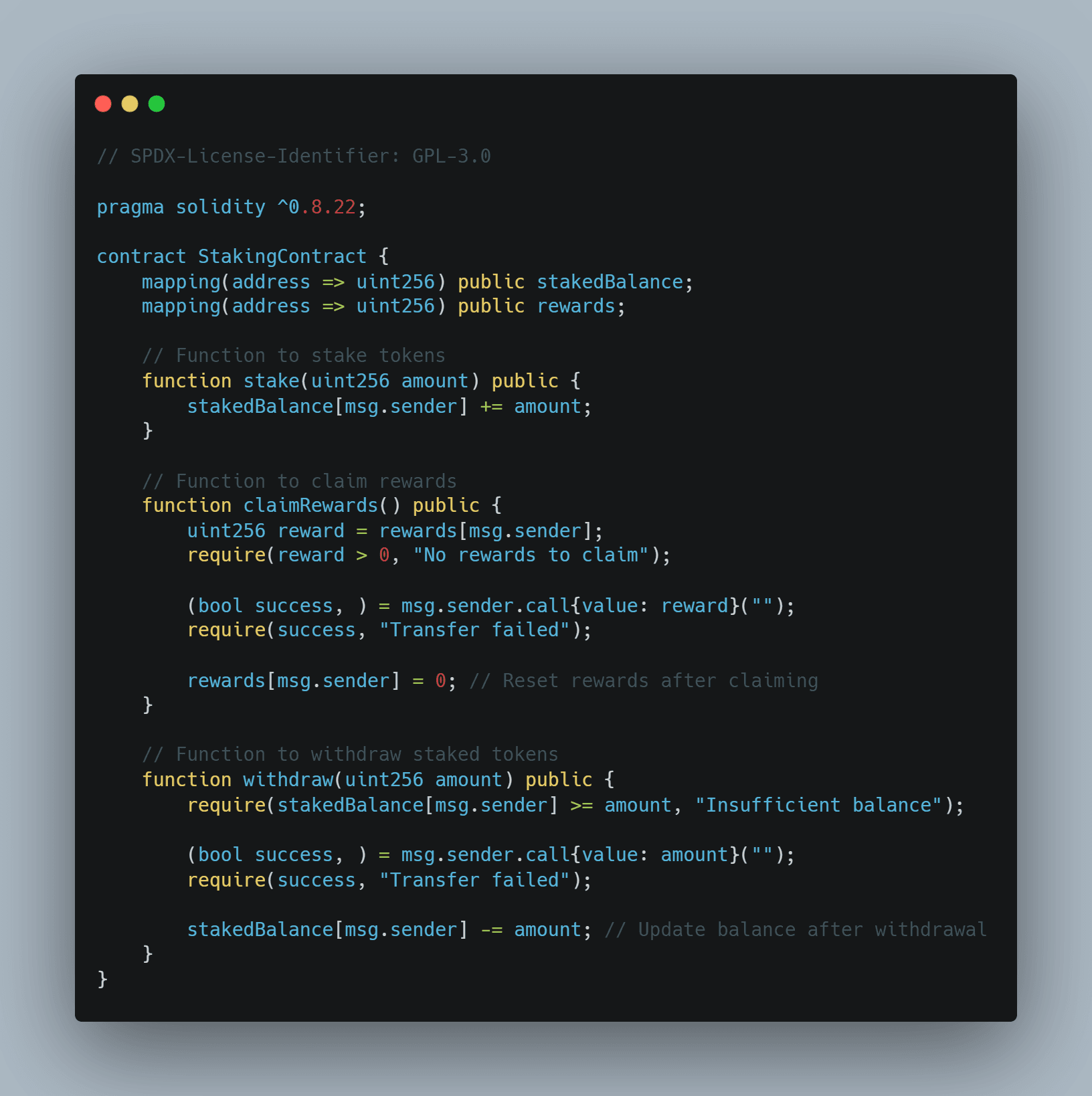
This section will break down a reentrancy attack into a clear, step-by-step process, using a simplified example. We'll look at vulnerable code, the attacker's malicious contract, and how the attack unfolds. Imagine a simple bank contract where users can deposit and withdraw Ether. The contract keeps track of each user's balance. A vulnerable implementation might first send the Ether to the user and then update the user's balance. This is where the reentrancy vulnerability arises. An attacker can create a malicious contract that calls the bank's withdraw function. Inside the malicious contract, upon receiving the Ether, the attacker's contract immediately calls the bank's withdraw function again,beforethe bank contract has had a chance to update the attacker's balance. This process can be repeated multiple times, effectively draining the bank contract of Ether. Let's say Alice has 5 ETH in the vulnerable contract. She calls `withdraw(2 ETH)`. The contract sends 2 ETH to Alice. Alice's malicious contract receives 2 ETH and immediately calls `withdraw(2 ETH)` again. Since the vulnerable contract hasn't updated Alice's balance yet, it still thinks she has 5 ETH. The contract sends another 2 ETH to Alice. This repeats until the contract is drained. The key to understanding this is the order of operations. The vulnerable contract sends the fundsbeforeupdating the state. This allows the attacker to re-enter the function and exploit the delayed update.
The History and Myths of Reentrancy Attacks
This section explores the historical context of reentrancy attacks, including famous incidents like the DAO hack. We'll also debunk common misconceptions and myths surrounding this vulnerability. The most infamous example is undoubtedly the DAO hack of 2016. The DAO (Decentralized Autonomous Organization) was a groundbreaking project that aimed to create a decentralized venture capital fund. Unfortunately, a reentrancy vulnerability in its smart contract allowed an attacker to drain a significant portion of the DAO's Ether holdings, leading to a hard fork of the Ethereum blockchain. The DAO hack was a watershed moment for the blockchain community, highlighting the critical importance of smart contract security. Before the DAO hack, reentrancy attacks were not widely understood or recognized as a serious threat. The incident served as a harsh lesson, prompting developers to prioritize security audits and adopt safer coding practices. It also led to the development of various tools and techniques for detecting and preventing reentrancy vulnerabilities. One common myth is that reentrancy attacks are only possible in complex smart contracts. While complex contracts may have more attack surfaces, even simple contracts can be vulnerable if they don't follow secure coding practices. Another myth is that using a specific programming language or framework automatically protects against reentrancy. While some tools may offer built-in protections, developers still need to be aware of the underlying principles and actively implement security measures. The DAO hack serves as a stark reminder that even seemingly well-designed contracts can be vulnerable to reentrancy attacks. Understanding the history and myths surrounding this vulnerability is crucial for developing a strong security mindset.
Hidden Secrets: Identifying Reentrancy Vulnerabilities
This section will dive into the technical details of identifying reentrancy vulnerabilities in smart contracts. We'll discuss code patterns that are particularly susceptible and techniques for manual and automated analysis. The hidden secret is that Reentrancy vulnerabilities often lurk in seemingly innocuous code. The most common red flag is any function that sends Ether to an external addressbeforeupdating its state. This "check-effects-interactions" pattern is a recipe for disaster. Look for instances where the contract calls `transfer()`, `send()`, or `call()` on an external address. Then, carefully examine the code path to see if the external contract has the opportunity to call back into the original contractbeforethe state is updated. Manual analysis is a crucial step in identifying reentrancy vulnerabilities. Start by carefully reviewing the contract's code, paying close attention to any functions that interact with external addresses. Look for the "check-effects-interactions" pattern and try to identify potential call stacks that could lead to a reentrancy attack. Automated analysis tools can also be helpful in identifying potential vulnerabilities. These tools can scan the code for common patterns and automatically flag potential issues. However, it's important to remember that these tools are not foolproof and should be used in conjunction with manual analysis. Understanding the underlying principles of reentrancy attacks is essential for effectively using these tools and interpreting their results. The ability to spot these vulnerabilities requires a deep understanding of the Ethereum Virtual Machine (EVM) and how smart contracts interact with each other. It's like learning to read the language of vulnerabilities, uncovering the hidden weaknesses within the code.
Recommendations: Preventing Reentrancy Attacks
This section will provide practical recommendations for preventing reentrancy attacks in your smart contracts. We'll cover various defense mechanisms and best practices. The most common and effective defense mechanism against reentrancy attacks is the "checks-effects-interactions" pattern, implementedcorrectly. But what is the recommendation for how to use them, and which ones are the best to use? What if there is an unknown type of attack coming in the future? Reversing the order of operations – updating the statebeforesending funds – eliminates the possibility of reentrancy. This ensures that the contract's state is always consistent, preventing the attacker from exploiting the delayed update. Another popular defense is using reentrancy guards. A reentrancy guard is a modifier that prevents a function from being called recursively. This can be implemented using a simple boolean variable that is set to `true` when the function is entered and set back to `false` when the function exits. If the function is called again while the variable is `true`, the transaction will revert. Using pull-over-push payments is also a recommendation. Instead of directly sending Ether to users, the contract allows users to withdraw their funds. This eliminates the need for the contract to call an external address, preventing the possibility of reentrancy. However, keep in mind that pull-over-push might not be the best solution in every case, as this creates another attack vector in the future, which might be costly to implement. Thoroughly auditing your smart contracts by experienced security professionals is crucial. Auditors can identify potential vulnerabilities that you may have missed. Consider using formal verification tools to mathematically prove the correctness of your smart contracts. Formal verification can help to identify subtle bugs and vulnerabilities that are difficult to detect through traditional testing methods. These are all important, yet can only act as a safety net, in the end you, as a developer, need to learn how these attacks work.
Further Deep Dive: Reentrancy Guard Implementation
Let's delve deeper into the implementation of reentrancy guards. How do they work under the hood, and what are the potential pitfalls? A reentrancy guard, at its core, uses a state variable (typically a boolean) to track whether a function is currently executing. Before executing the function's logic, the guard checks if the variable is set. If it is, it means the function is already in execution (re-entered), and the transaction is reverted. If not, the variable is set, the function's logic is executed, and finally, the variable is reset. This ensures that the function can only be entered once at a time, preventing reentrancy.
For example:
```solidity
bool private _not Entered;
modifier non Reentrant() {
require(_not Entered, "Reentrant call");
_not Entered = false;
_;
_not Entered = true;
}
function withdraw(uint amount) public non Reentrant {
// ... function logic ...
}
```
In this example, the `non Reentrant` modifier is applied to the `withdraw` function. The modifier first checks if `_not Entered` is `true`. If it's not, the transaction reverts with the message "Reentrant call". Then, it sets `_not Entered` to `false`, executes the function's logic (`_;`), and finally sets `_not Entered` back to `true`. While reentrancy guards are effective, they are not a silver bullet. Incorrect implementation can lead to vulnerabilities. For example, if the state variable is not properly reset after the function's execution, the function may become permanently locked, preventing legitimate users from accessing it. Moreover, reentrancy guards only protect against reentrancy within the same contract. They do not prevent reentrancy from other contracts. Therefore, it's essential to carefully consider the potential attack vectors and implement appropriate security measures. Reentrancy guards are a valuable tool in the arsenal of smart contract developers, but they should be used in conjunction with other security best practices.
Tips and Tricks for Writing Secure Smart Contracts
This section will share valuable tips and tricks for writing secure smart contracts, focusing on avoiding common pitfalls and adopting a security-first mindset. When starting out, always, always start small. Don't build grandiose plans, instead build the simplest contract you can think of, deploy it to a testnet, and start tinkering with it. You will be surprised at how much you learn from this process. Another critical trick is to embrace the "fail-fast" principle. This means writing code that is designed to detect errors early and revert transactions before any damage can be done. Use require statements liberally to enforce invariants and validate inputs. Don't be afraid to revert transactions if something doesn't look right. A secure contract is one that protects users' funds and data, even if it means sacrificing some efficiency. When dealing with external calls, always be mindful of the potential for reentrancy. Apply the "checks-effects-interactions" pattern religiously, and consider using reentrancy guards for critical functions. Thorough testing is essential for identifying potential vulnerabilities. Write comprehensive unit tests that cover all possible scenarios, including edge cases and error conditions. Use fuzzing tools to automatically generate a large number of random inputs and test the contract's behavior. Security audits are also crucial. Engage experienced security professionals to review your code and identify potential vulnerabilities. Audits can provide valuable insights and help you to improve the security of your smart contracts. Remember that security is an ongoing process. As your smart contracts evolve, you need to continuously monitor them for potential vulnerabilities and adapt your security measures accordingly. This involves staying up-to-date with the latest security threats and best practices, and actively engaging with the security community. Writing secure smart contracts is a challenging but rewarding endeavor. By following these tips and tricks, you can significantly reduce the risk of vulnerabilities and protect your users' assets.
Advanced Topics: Cross-Function Reentrancy
While the classic reentrancy attack involves calling the same function recursively, cross-function reentrancy presents a more subtle and often overlooked threat. Cross-function reentrancy occurs when one function in a contract calls an external contract, which then calls back into adifferentfunction within the original contract, exploiting a shared state. This can be particularly dangerous because the developer might assume that only the originally called function needs reentrancy protection. Let's say a contract has two functions, `deposit()` and `withdraw()`. `deposit()` might update a user's balance and then emit an event. `withdraw()` might send Ether to the user and then update their balance. If `deposit()` calls an external contract that, in turn, calls `withdraw()`, it can lead to unexpected behavior if the user's balance has not yet been updated by the `deposit()` function. To prevent cross-function reentrancy, it's crucial to consider the potential interactions between all functions in the contract and to apply reentrancy guards or the "checks-effects-interactions" pattern to all functions that modify shared state. In the above example, a reentrancy guard on either `deposit()` or `withdraw()` might not be enough if the shared state (the user's balance) is not updated consistently. Instead, the checks-effects-interactions pattern should be applied diligently inbothfunctions. This involves updating the user's balancebeforeemitting the event in `deposit()`, andbeforesending Ether in `withdraw()`. Cross-function reentrancy highlights the importance of a holistic approach to smart contract security. It's not enough to simply protect individual functions; you need to consider the entire contract and how its functions interact with each other.
Fun Facts About Reentrancy Attacks
Did you know that the term "reentrancy" isn't exclusive to blockchain? It's a concept that has been around in computer science for decades! Now, how exactly would that work? The concept of reentrancy actually predates blockchain by quite a bit. In computer science, reentrancy refers to a subroutine or function that can be safely called again while it is already executing. This is important in multi-threaded environments, where multiple threads might try to access the same function simultaneously. In the context of smart contracts, reentrancy takes on a more specific meaning, referring to the vulnerability where an external contract can call back into the original contract before the original function has completed its execution. One fun fact is that the DAO hack, which was caused by a reentrancy vulnerability, led to a hard fork of the Ethereum blockchain, resulting in the creation of Ethereum Classic. This highlights the significant impact that reentrancy attacks can have on the blockchain ecosystem. Another interesting fact is that the "checks-effects-interactions" pattern, which is the most common defense against reentrancy attacks, is actually a generalization of a more fundamental principle called "separation of concerns." Separation of concerns involves dividing a program into distinct sections, each of which addresses a separate concern. In the context of smart contracts, this means separating the logic for checking preconditions, updating state, and interacting with external contracts. Reentrancy attacks are not just a theoretical threat; they have caused significant financial losses in the past. By understanding the history and impact of these attacks, developers can better appreciate the importance of smart contract security and take steps to prevent them from occurring in their own code. It's a fascinating intersection of computer science principles and real-world financial consequences.
How to Debug Reentrancy Attacks
This section will provide practical guidance on debugging reentrancy attacks, including tools and techniques for identifying the root cause of the vulnerability. Debugging reentrancy attacks can be challenging, but it's essential for understanding how the vulnerability works and how to fix it. The first step is to reproduce the attack. This involves creating a test environment that mimics the conditions under which the attack can occur. You'll need to deploy the vulnerable smart contract and the attacker's malicious contract to a local blockchain, such as Ganache. Use a debugger such as Remix, Truffle or Hardhat to step through the code and observe the flow of execution. Pay close attention to the call stack and the state of the contract's variables at each step. This will help you to identify the point at which the reentrancy occurs. Remix IDE is a very popular and useful tool to trace the transaction. You can step through each line of code, inspect variables, and analyze the call stack. The "execution cost" feature in Remix can also be helpful for identifying gas-intensive operations that might be vulnerable to reentrancy. Truffle and Hardhat are excellent tools for automated testing and debugging. You can write unit tests that specifically target reentrancy vulnerabilities. These tests can help you to quickly identify and fix bugs. Furthermore, they can be used for regression testing to ensure that fixes for reentrancy vulnerabilities do not introduce new issues. Once you've identified the root cause of the vulnerability, you can start to develop a fix. Apply the "checks-effects-interactions" pattern, use reentrancy guards, or implement pull-over-push payments. After applying the fix, thoroughly test the contract to ensure that the vulnerability has been eliminated and that no new issues have been introduced. Debugging reentrancy attacks requires a combination of technical skills, analytical thinking, and a deep understanding of the EVM.
What If Reentrancy Attacks Continue to Evolve?
This section will speculate on the future of reentrancy attacks and how they might evolve as blockchain technology advances. What if we get new types of Virtual Machines in the future that support more complex functionality. What new kinds of vulnerabilities could be born? Reentrancy attacks are a persistent threat to smart contracts, and as blockchain technology evolves, so too will the tactics used by attackers. It's likely that we'll see more sophisticated forms of reentrancy attacks that are harder to detect and prevent. One potential area of evolution is cross-chain reentrancy attacks. As more blockchains become interconnected, attackers could exploit vulnerabilities that span multiple chains. For example, an attacker could use a reentrancy vulnerability on one chain to manipulate the state of a contract on another chain. Another possibility is the emergence of reentrancy attacks that target new features and functionalities in smart contracts. As smart contracts become more complex and incorporate features such as oracles, De Fi protocols, and NFTs, attackers will likely find new ways to exploit these features through reentrancy. To stay ahead of these evolving threats, developers need to adopt a proactive security mindset and continuously monitor their smart contracts for potential vulnerabilities. This involves staying up-to-date with the latest security threats and best practices, and actively engaging with the security community. It also involves using advanced security tools and techniques, such as formal verification and automated vulnerability scanners. Furthermore, it's crucial to design smart contracts with security in mind from the outset. This involves following secure coding practices, implementing robust access controls, and minimizing the attack surface. By taking a proactive and holistic approach to security, developers can significantly reduce the risk of reentrancy attacks and protect their users' assets.
Listicle: Top 5 Reentrancy Prevention Techniques
Here's a concise list of the top 5 techniques to safeguard your smart contracts from reentrancy attacks: What would be the summary that includes the key elements of the topic, but does not go too deep? 1.Checks-Effects-Interactions Pattern: Always update the contract's statebeforeinteracting with external contracts. This prevents the attacker from re-entering the function before the state is updated.
2.Reentrancy Guards: Implement a modifier that prevents a function from being called recursively. This ensures that the function can only be entered once at a time.
3.Pull over Push Payments: Allow users to withdraw their funds instead of directly sending Ether to them. This eliminates the need for the contract to call an external address.
4.Limit External Calls: Minimize the number of external calls in your smart contracts. The fewer external calls, the smaller the attack surface.
5.Security Audits: Engage experienced security professionals to review your code and identify potential vulnerabilities. Audits can provide valuable insights and help you to improve the security of your smart contracts. These techniques are not mutually exclusive and should be used in combination to provide a robust defense against reentrancy attacks. Remember that security is an ongoing process and that you need to continuously monitor your smart contracts for potential vulnerabilities. Consider using formal verification tools to mathematically prove the correctness of your smart contracts. Formal verification can help to identify subtle bugs and vulnerabilities that are difficult to detect through traditional testing methods. Stay up-to-date with the latest security threats and best practices, and actively engage with the security community. By following these techniques, you can significantly reduce the risk of reentrancy attacks and protect your users' assets. If you do not have a security audit, you are not being safe. If you do not have pull over push payments, it is possible, but should be highly considered.
Question and Answer About Reentrancy Attacks
Here are some common questions and answers about reentrancy attacks:
Q: What is the difference between reentrancy and cross-function reentrancy?
A: Reentrancy involves calling the same function recursively, while cross-function reentrancy involves calling a different function within the same contract before the original function has completed.
Q: Are reentrancy guards foolproof?
A: No, reentrancy guards are not foolproof. They only protect against reentrancy within the same contract and can be bypassed if implemented incorrectly.
Q: What is the "checks-effects-interactions" pattern?
A: It's a coding pattern where you perform checks (validate inputs), update state (effects), and then interact with external contracts. This order prevents reentrancy vulnerabilities.
Q: How can I test my smart contracts for reentrancy vulnerabilities?
A: You can write unit tests that specifically target reentrancy vulnerabilities, use fuzzing tools to generate random inputs, and engage experienced security professionals to perform security audits.
Conclusion of A Beginner’s Guide to Reentrancy Attacks
Reentrancy attacks are a serious threat to smart contract security, but by understanding the underlying principles and implementing appropriate defense mechanisms, developers can significantly reduce the risk of these vulnerabilities. The "checks-effects-interactions" pattern, reentrancy guards, and pull-over-push payments are all valuable tools in the fight against reentrancy attacks. Remember that security is an ongoing process and that you need to continuously monitor your smart contracts for potential vulnerabilities. By staying up-to-date with the latest security threats and best practices, and actively engaging with the security community, you can help to ensure the safety and security of your smart contracts and the blockchain ecosystem as a whole. The importance of understanding the history of smart contract hacks, and how they evolved is crucial for adapting to new threat models that could come in the future.